Scams
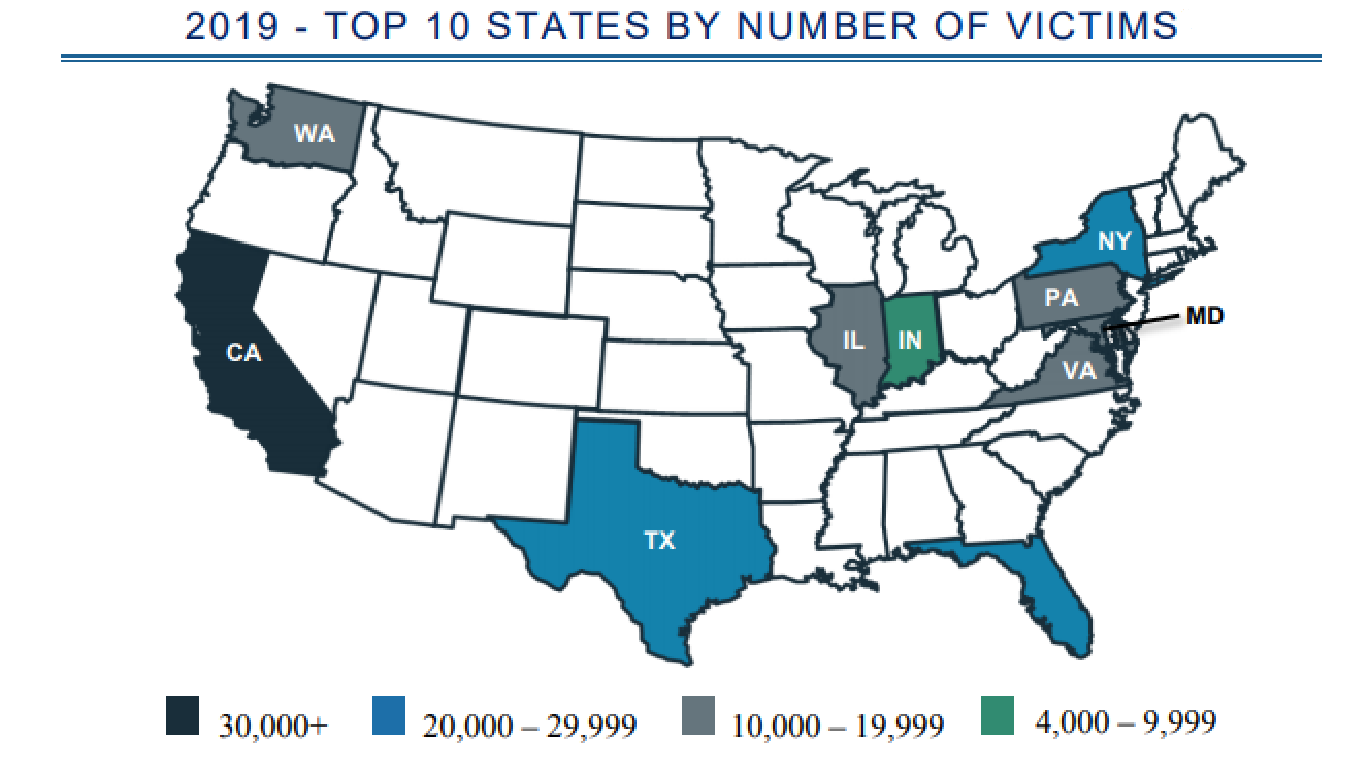
Internet scams are one of the most infamous forms of crime that occurs on the internet. When the idea of internet scams are mentioned, most people think of an old lady fending $10,000 to a “Nigerian Prince” with promises of receiving more in return. The truth is that Internet scams and fraud have been evolving. According to statista.com[1] the age groups that report the highest amount of internet fraud in descending order are 60-69, 50-59, and 30-39. Additionally, the FBI[2] defines seven core types of internet fraud. Ioana Rijnetu at Heimdal Security[3], an online company, further defines and breaks down internet fraud into 19 variants. Further U.S. based scams statistics include: 3.5 billion dollars were lost to internet fraud in 2019 alone, the FBI receives an average of 1,200 reports of internet fraud a day. The states with the most reported cases of internet fraud, in descending order, are California, Florida, Texas, New York, and Washington.
According to the FBI, the three most common internet scams are, in descending order, phishing, non-payment/non-delivery, and personal data breach. Phishing is a scam where a scammer sends emails or social media messages masquerading as a major company or website to obtain a user’s login information. In 2014 Sony was a prominent victim of phishing after the tactics were used on several of their employees with the login information obtained being subsequently used to leak several of their upcoming films. The attack cost Sony 100 million dollars, according to Computerworld[4].
Non-payment/non-delivery is a scam by which a user of an online marketplace such as eBay and buys or sells an item without receiving payment or the item, depending on which scam it is. The FBI defines a personal data breach scam as “A leak or spill of data which is released from a secure location to an untrusted environment. Data breaches can occur at the personal and corporate levels and involve sensitive, protected, or confidential information that is copied, transmitted, viewed, stolen, or used by an individual unauthorized to do so.”
While the 2013 Adobe leak is the case of this in recent memory that impacted the most users at 153 million, the Equifax leak is more famous for leaking Social Security numbers, addresses, birth dates, and in some cases drivers' license numbers, as summarized by Dan Swinhoe in an article for CSO Online[5].
Despite their prolific nature, you can lower your chances of being a victim of one of these scams and/or minimizing their damage in some simple ways. When identifying a phishing email, the first thing to do is to check the sender. According to Ana Dascalescu at Heimdal Security[6], typical phishing emails are sent from non-official email addresses, for example, Amazon’s email address is “noreply@amazon.com” while an Amazon phishing email may come from “AmazonUpdate@efficaciouscrbays.xyz”. Also look out for suspicious contents, request for information they should already know, urgency, requests to call an outside number, etc. When it comes to non-payment/non-delivery scams, the FBI[7] suggests only doing business with reputable sites, confirming the sellers listed phone numbers or email is active while avoiding those who don't list them, and checking the reputability of sites with outside sources like other sites, users, and even the Better Business Bureau.
Ads
The internet is one of the greatest tools for modern advertisers and ads are the reason that content on the internet is largely free. It is in view of this symbiotic relationship that we must discuss advertising on the internet and more specifically Malicious Ads.
The Center for Internet Security[8] defines malicious advertising or “Malvertising” as, “the use of online, malicious advertisements to spread malware and compromise systems.” In a report for Vice[9], Lorenzo Franceschi-Bicchierai reported that the rate that criminals were paying to server malicious ads on major sites was as low as 0.13$ per 1000 views. Bicchierai also shares other troubling statistics like malvertising being up 260% in the first half of 2015 compared to 2014. Additionally, Bicchierai reports that 13% of victims of malvertising pay the ransom that malicious ads demand of users, such ransoms are often up to 500$. Using the stats that we’ve established, a criminal with $500 in malvertising with a $100 ransom and a 1% ransom acceptance rate, and a rate of $0.13 per 1000 views could turn their $500 into $3.85 million dollars after rounding!
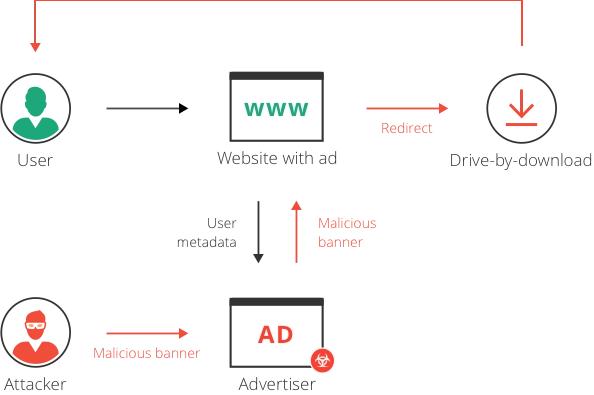
We now know what malicious ads or Malvertising is but how does it work? Malvertising is a delivery method for ransomware, a type of virus that holds a user’s data and computer hostage by blocking access until they pay a ransom. The goal is to install ransomware which it accomplishes by sending users ads. The way these ads work is by burying within the otherwise safe ad code to redirect the user’s system to a server where an exploit kit is installed; the exploit then evaluates the user’s system and finds vulnerabilities that are exploited to take control of the system and hold it ransom, as explained by Dilan Samarasinghe in his article for the Center for Internet Security[10].
In addition to ransomware, malicious ads may also install adware onto a user’s system. Adware is malicious software that serves a user more ads than normal and mine’s a user’s system for sensitive data, as detailed by Imperva[11] in their Malvertising article.
With both the knowledge on what malvertising is and how it works, the question becomes “how do you protect yourself from it?” Due to the why malvertising works it can be hard to ensure you stay protected from it but there are some steps you can take. One thing is to make sure that you keep the web browser extensions up-to-date to make use of their built-in security measures. Additionally, try to close any extraneous tabs, they cycle their ads even when you aren’t viewing them so keeping as few tabs open as possible limits your chances of encountering a malicious ad. Whenever you’re using a computer it’s always a good idea to having antivirus software installed and up to date. A final method that not all users may want to use is ad blockers, ad blockers block scripts on web pages that run ads and thus, stop malicious ads from ever reaching the user but they also stop sites from making ad revenue which some individuals don’t agree with. There is also the chance that some sites employ ad-blocker-blocker which won’t allow users with ad-block to view their pages. All these methods are presented as laid out on imperva.com[12].
Bots
The internet is defined by its many, many users but a large number of those users aren’t really users at all; they’re bots. What are bots? Simply put bots are robots made by people to imitate people online. Spam accounts are similar accounts either controlled by a person to post repetitive content to achieve some means or a bot doing the same. Why do spam and bot accounts matter? Spam and bot accounts matter because they can easily be used to create the illusion of mass support behind an idea.
A novel example of this is the 1988 Batman story A Death in the Family, this comic story presented the idea that Batman’s sidekick Robin would be put in peril with fans having the ability to choose if he’d live or die. There was one phone number for life and one for death. In the end, there were 10,614 votes and death won with 5,343 votes. With this info, you might assume comic readers wanted Robin to die when in fact, one fan had set his computer to call the “die hotline” every 90 seconds for eight hours swinging the vote, as explained by then Batman editor Dennis O’Neil[13]. What this fan did is an example of vote botting where one uses a bot to generate votes in a poll. In this case, a bot influenced something largely meaningless like the status of a comic book character but when similar bots are used in more important polls or to support an agenda the prospects get far grimmer.
So how do bots and spam accounts work and what can they do? Spam accounts and bots are very simple mechanically. They typically execute on a “script” or simple repetitive computer program. Scripts can be customized to do a wide variety of things but some popular examples are like and comment bots which can be used to give a social media post lots of likes or comments drawn from a pre-made list, as explained by this article from smarterdigitalmarketing.co[14].
These types of bots are used to create false engagement or the appearance that a post or person on social media is popular which often makes real people more likely to engage and believe other real people are already doing so. There are also “utility bots”or bots created to do something for users on social media without hiding that they are bots.
An example of this type of bot would be a bot that provides download links for videos on platforms like Facebook or Twitter. This type of bot is harmless and more to the point helpful as they provide a transparent service to online communities, as explained on botnerds.com[15].
A third prominent bot type is the spam bot which exists to post repetitive content online, as explained on botnerds.com[16]. These bots can be used for an assortment of purposes but the most prominent today would be linking to articles. Tons of spambots today will spam links to articles and other off-site media to try and get the originator’s attention. These types of bots are often used to spread fake news, as discussed by Simon Thorpe in his article for securitybulivard.com[17].
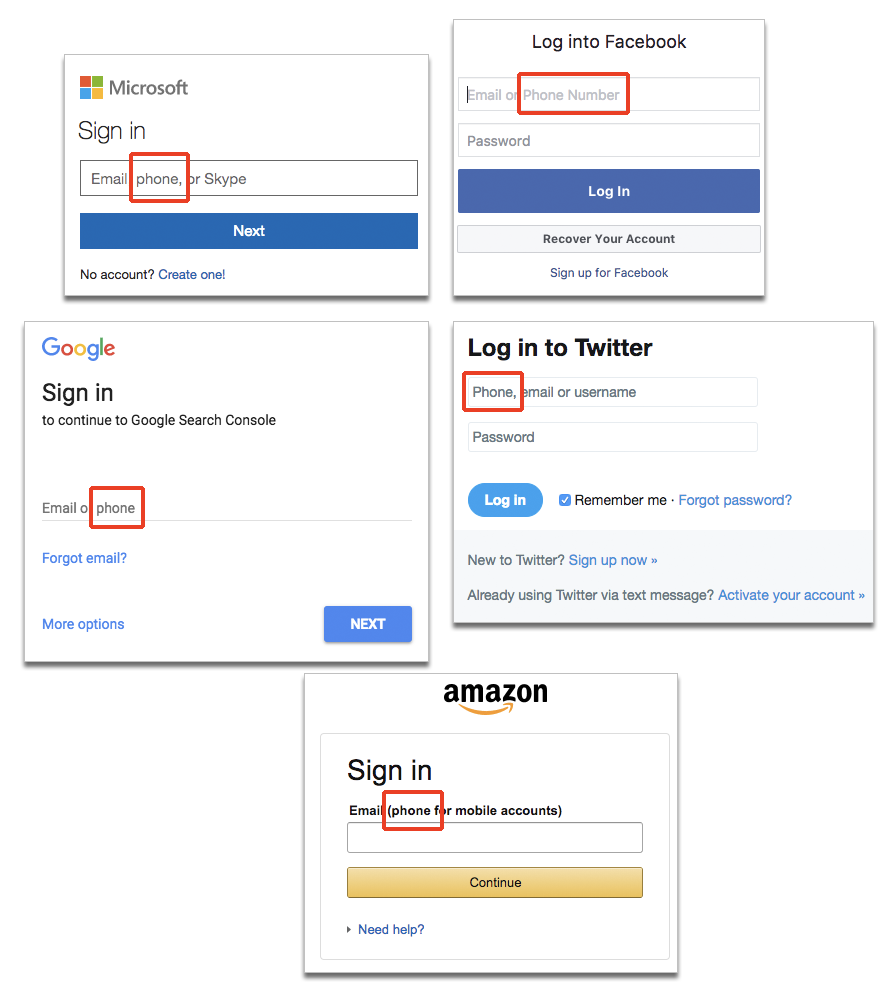
With all this said, the question becomes “What can I do to stop bot accounts?” And the answer’s pretty simple: “Not a lot.” Due to their easy to create nature, bot and spam accounts will always exist en masse. What you can do is learn how to recognize bots. The watch signs for bots according to Luciano Hernández in his article for f-security.com[18] are, “if the profile posts frequently and around the clock, is very new, has random characters and numbers in their account name, have no profile picture or bio included or follows a certain pattern when compared to other accounts. After recognizing a bot, it's important that you stop engaging with the bot and report it. Though it’s a largely Sisyphean task, platforms like Twitter and Facebook are trying to purge the bots from their sites. While that about all individuals can do to help with the bot problem on social media it is important to note that platforms are trying to remedy the problem. The popular method is the slow shift from having social media accounts being tied to an email to being tied to a phone number, instead. This would reduce the number of bots as it’s far harder and more expensive for spammers to create phone numbers than it is to create emails, paraphrase from Simon Thorpe of securityboulevard.com[19].